Wait For The Day
Description
Momma bought a Christmas gift for you. She says it's something you love! But Christmas is like more than 6 months away :/ Try to peek in and find out what the gift is, before the Christmas eve ;)
TL;DR
Patch binary to bypass checks
Run binary through gdb to get flag in memory
Get flag
Solution
Analysis
We are given a file with no extension. Running file gift_for_you returns that it is a binary file, so change permissions to allow it to be executable.

For such challenges, I would usually run the binary first to see what it does (don't run untrusted software >_>).
We see the following result without the need to supply any user input.

Firing up ghidra, we can analyze the main function of the binary.

The binary performs some check against the current time of the local system. It checks using a custom function time_check and if the function returns a 0 and this DISPATCH_GIFT variable is equal to 0xff, then this dispatch_gift function will be called with the format as the flag as parameters.

So we know that dispatch_gift is the function that returns the flag. Let's check the decompiled code of that function.

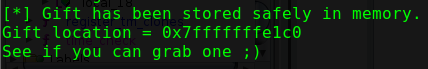
This is too much code for me to spend my limited time to try to understand, but one of the line that caught my attention is "Gift has been stored safely in memory".
Since the "Gift" or flag is stored in memory when the binary is running, and the dispatch_gift function is not affected by the time_check function, we can thus patch the binary to jump straight past the time_check function and straight to dispatch_gift. Then we can find the flag in memory through gdb.
Patching The Binary
I used Radare 2 to patch the binary.
Run
r2 -A -w gift_for_youto 'write' on the binary.Run
aaaato run all analysis on the binary (usually not necessary).Step into the main function with
s main.

Run
pdfto view themainfunction in assembly.Find the first jump instruction (jmp,je,jne etc.) and note the address of it. This is the first
ifstatement we see inghidraand we want to patch it to jump straight to the address where it gets ready to calldispatch_gift.Then find the address where it gets ready to call
dispatch_gift.
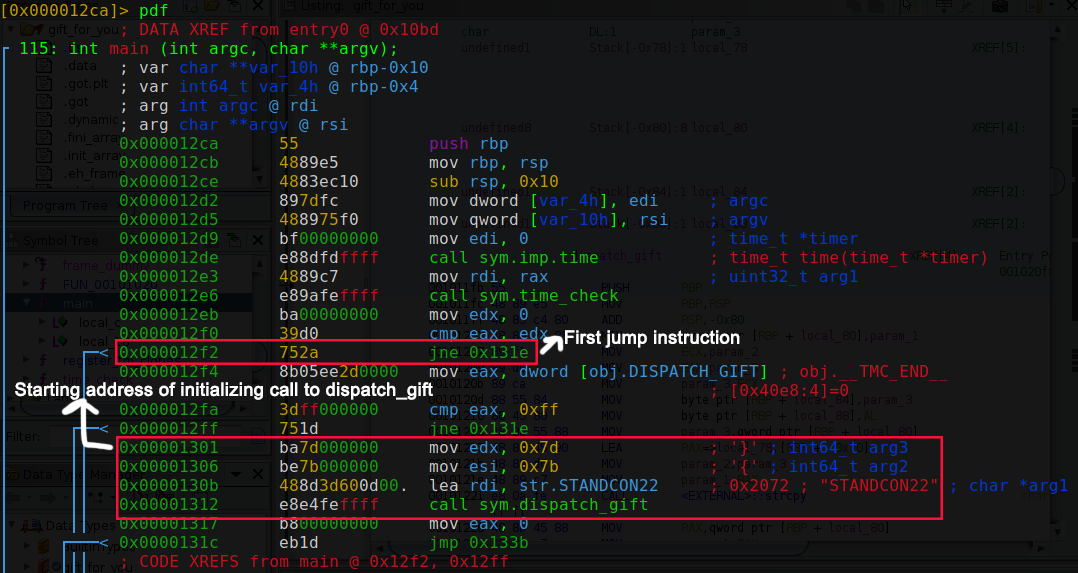
Step into the jump address we got by running the command
s 0x12f2.Patch instruction to jump to dispatch_gift by running
wa jmp 0x1301, then quit withq.

Now running the binary again, we can see that the output is different, means we successfully patched it!

Getting flag from memory
Run the binary through gdb:
gdb gift_for_youSet a breakpoint at dispatch_gift:
break dispatch_giftRun the binary:
runProgram should break at breakpoint
Disassemble dispatch_gift to find return address to break at:
disass dispatch_gift, thenbreak *<ret addr>

Continue the execution:
cProgram should break at ret (breakpoint 2)
There should be an address returned by the binary on where the flag is at. Print the value at the address in string format by running
x/s <addr>, or if you are usinggdb-pwndbg, you can just runsearch "STANDCON".

Last updated